Key Takeaways of Microsegmentation
- Aggressive network segmentation is a key component of a zero-trust architecture.
- Implementing microsegmentation reduces attack surface and limits attacker mobility within the network.
- A comprehensive understanding of your network architecture is required for microsegmentation prioritization
- Zero-trust principles are more commonly being implemented with identity and device-based controls
- Although it adds complexity, microsegmentation will allow you to derive more granular access and achieve more detailed visibility.
- Stakeholder input and risk analysis should inform your microsegmentation phasing.
- Avoid misalignment between network maintenance and microsegmentation priorities.
- It’s acceptable to scale your microsegmentation efforts over time.
The Importance of Microsegmentation
A zero trust architecture requires aggressive network segmentation.
Segmenting defines where systems and users are connected. In the spirit of zero trust, you want systems to connect to other systems only if they are appropriately authorized. These restrictions are used to limit the impact of potential cyber attacks when unauthorized access occurs.
The most granular approach is called microsegmentation, which is when distinct governance modules are applied at the level of devices, applications, and workloads.
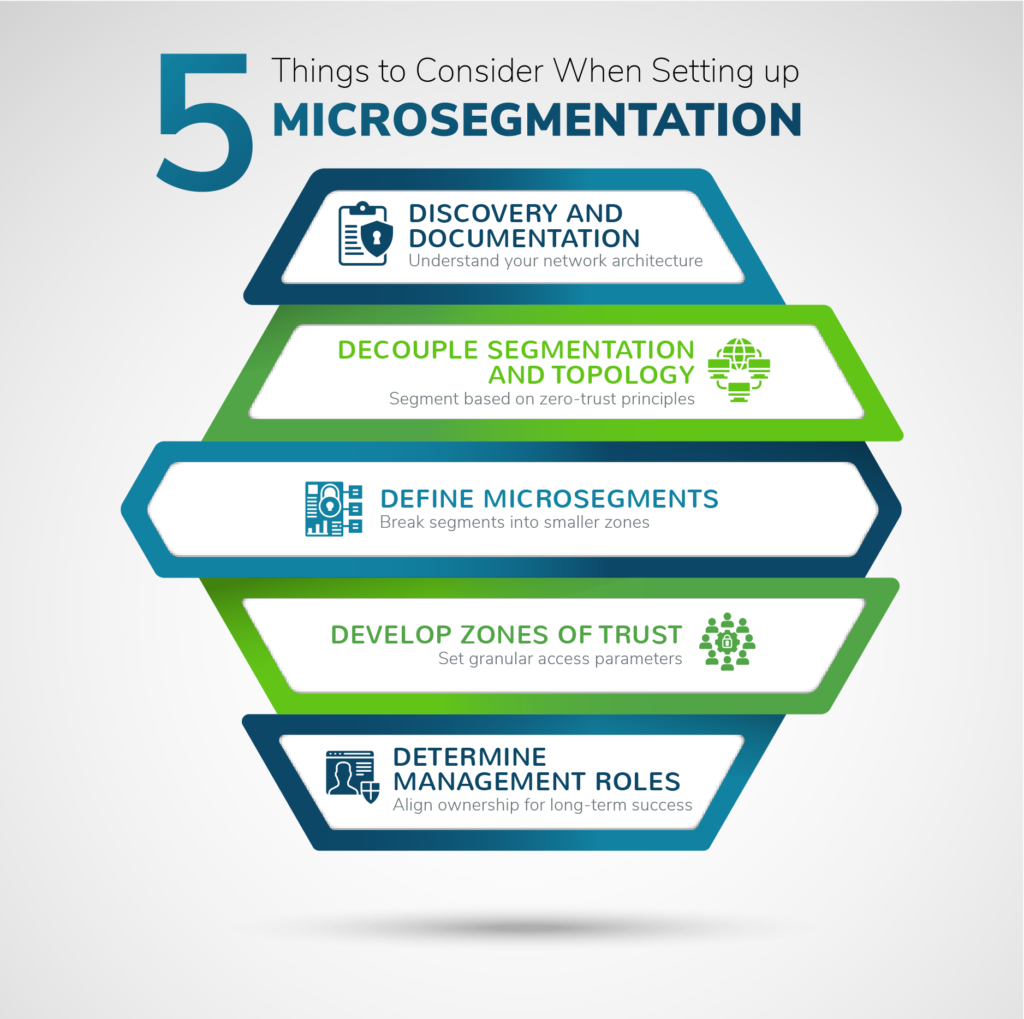
Step One: Discovery and Documentation
The most important part of a successful microsegmentation implementation is a detailed understanding of your network architecture. You must determine what devices are connected and which applications are running on the network, and then map the data and traffic flows. A robust discovery and documentation process will enable prioritization of your efforts.
Step Two: Decouple Segmentation and Topology
An approach to segmentation that relies on network topology and addresses will create administrative overload. Using VLANs and restricting communications with firewalls and access control lists require resources to be constantly available to implement configuration changes. In addition, address-based approaches are less secure and are not extensible to cloud environments.
A nimble environment that is resistant and resilient to attack, but with minimal administrative burden cannot be segmented based on network topology. Zero-trust principles are increasingly being implemented using identity and device-based controls, instead.
Step Three: Define Microsegments
Now that your network architecture is documented and prioritized, you can use your defined security policies, and develop smaller security zones. This gives you the ability to apply traditional segmentation tactics at a more granular level.
Be aware that you are creating additional complexity and make sure you are proceeding in an organized and logical way. Although it may feel counter-intuitive, the increased complexity will allow you to derive more granular access, achieve more detailed visibility, reduce vulnerability risk, and is a key step to facilitate your microsegmentation approach.
Step Four: Develop Zones of Trust
To establish zones of trust requires a balancing act between how granular the segmentation becomes and the ability to manage the new configurations. The goal is to improve security without impacting operations or creating access issues. The segmentation logic must be sound, and should be developed with input from stakeholders including the architecture development team, operations and security.
Decisions about policies, segmentation categories, and the security controls should address risk appetites and the value of the assets within each segment.
Step Five: Determine Management Roles
One of the most common pitfalls of microsegmentation is organizational misalignment with reference to the day-to-day maintenance of a microsegmentation program. Microsegmentation policy execution and management are continuous activities, and the meticulous documentation, implementation, and assignment of roles and responsibilities is paramount. Support for the initiative and identification of ownership will position your microsegmentation framework for long-term success.
Scale Your Microsegmentation
The easiest way to avoid being overwhelmed and end up abandoning a microsegmentation framework is to develop a phased approach to implementation. Scaling efforts can be prioritized by starting with targeted “crown jewel” applications and assets. Identify the highest value and highest risk areas of the network, and apply a microsegmented network structure to those first. Another option is to phase in microsegmentation in conjunction with the addition of new applications. It may be easier to implement your segmentation initiatives within modern applications that have been developed with a microservices approach.
Be mindful that microsegmentation does not have to be all or nothing. A crawl, walk, run approach offers a logical progression that can ease the administrative burden for your IT and Security teams. Start with a small, well-defined scope, monitor and evaluate for a predetermined period of time, inform the process with lessons-learned, and then move into broader implementation efforts.
Any steps that you take towards a microsegmented network have the ability to reduce your risk and minimize the available attack surface for cybercriminals.
Do you have questions about how to best implement microsegmentation in your network? Contact us to talk with one of our experts.